kCTF VRP Setup
We invite you to demonstrate an exploit against our kCTF demo cluster based on the challenges presented on this page. Successful demonstrations which don’t use Linux kernel vulnerabilities are eligible for rewards as described in our kCTF VRP announcement blog post.
Important note: If you’d like to demonstrate an exploit against a Linux kernel vulnerability, please submit it to our kernelCTF program. kCTF VRP does not accept Linux kernel vulnerabilities anymore since 2023-06-14. For more information read our blog post “Learnings from kCTF VRP’s 42 Linux kernel exploits submissions”.
kCTF is an open source infrastructure for CTF competitions. You can find details on how it works in the kCTF documentation, but in short, it’s running on a hardened Kubernetes cluster with the following security features:
- The OS and Kubernetes versions are upgraded automatically.
- The nodes are running Container-Optimized OS.
- Pod egress network access is restricted to public IPs only.
- Workload Identity restricts access to service accounts and the metadata server in addition to the network policies.
- Every connection to a challenge spawns a separate nsjail sandbox to isolate players from each other.
At present, we’re interested in two attack scenarios against this infrastructure:
- Breaking out of the nsjail sandbox as it would allow solving challenges in unintended ways.
- Breaking the isolation that Kubernetes provides and accessing the flags of other challenges.
For this purpose, we set up two kCTF challenges with secret flags: “kctf” and “full-chain”. You can demonstrate a working exploit by leaking the flags of either of these. You can find the code for the challenges here.
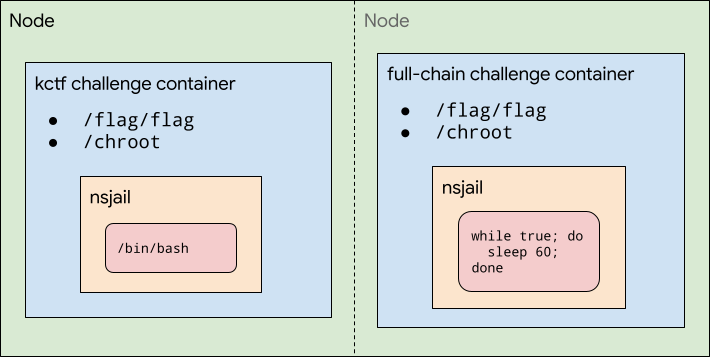
kctf challenge
The “kctf” challenge is the only entry point to the cluster. You can connect to it via:
Older cluster (GKE Regular release channel):
socat FILE:`tty`,raw,echo=0 TCP:kctf.vrp.ctfcompetition.com:1337
Newer cluster (GKE Rapid release channel):
socat FILE:`tty`,raw,echo=0 TCP:kctf.vrp2.ctfcompetition.com:1337
It will ask you to solve a proof-of-work and then gives you access to a bash running in a setup similar to the kCTF pwn template challenge. The only difference is that the flag is not accessible inside of the nsjail sandbox and you will need to break out of the chroot in order to read it. You can observe the full source code here.
The details of the environment of the VM can be read from /etc/node-os-release, and you can get the image of the VM following this script based on the output of /etc/node-os-release.
full-chain challenge
The “full-chain” challenge is a challenge that runs a while sleep loop and doesn’t have any exposed ports. In order to get access to the flag, you will need to break out of the “kctf” challenge and break the pod isolation of the cluster.
Flags
The flags are stored in Kubernetes secrets and mounted to the filesystem of the two challenges at “/flag/flag”. They are of the format:
KCTF{$CHAL_NAME-$TIMESTAMP:$MAC}
As you can see, the flags include a timestamp and are rotated frequently.
Submission
We want to avoid learning about unfixed vulnerabilities, so the process to submit reports is:
- Test your exploit - we recommend you to test it locally first, and run a GKE cluster to debug.
- If it is a 0day (there’s no patch for it yet), then send us a checksum of your working exploit to our form here. You won’t share any technical details about the vulnerability, you will just record the fact you found something (as we only reward the first person that writes an exploit for a given bug, we use it to resolve the timing in case of an exploit collision). Make sure to submit the exploit checksum before there’s a public patch and to submit the full exploit within a week after the patch is public. If you take longer than a week, we might issue the reward to someone else.
- For 1days or once there is a public patch, test your exploit it on the lab environment. If you have troubles let us know in #kctf and we’ll help you figure out any problems.
- Once you get the flag, send it together with the patch and the exploit here.
- To increase the timely sharing of new techniques with the community, we are also now requiring that the exploits that receive innovation bonus get publicly documented within a month, otherwise we may publish it.
Notes
We want to encourage the community to help research vulnerabilities, but which are still unfixed since they have not been shown to be exploitable. As such:
- The person that develops the exploit and receives the reward might not be the same as the person that discovered or patched the vulnerability.
- It’s ok to use 1-day exploits against the lab environment using publicly known vulnerabilities that exploit the patch gap between the time when a patch is announced and the lab environment is updated, however we will only issue a single reward per vulnerability.
When we receive an exploit for a fixed vulnerability we’ll add details here.
In case of questions or suggestions, you can reach us in #kctf.